Privacy protection and information security risk management
To protect the company's R&D achievements and customer's personal data, HTC emphasizes that protecting information security and privacy is the responsibility and mission of every employee. HTC has incorporated information security and personal data protection policies into its corporate culture and core values, and complies with all relevant information security and applicable privacy protection regulations in various countries.
To effectively control potential risks associated with personal information and information systems, HTC continuously optimizes its Privacy Information Management System and Information Security Management System. A dedicated team, comprised of departments such as Legal, Product Security, and Information Security, is responsible for driving privacy protection and information security initiatives.
Privacy Information Management System
Structure of HTC Privacy Information Management System (PIMS)
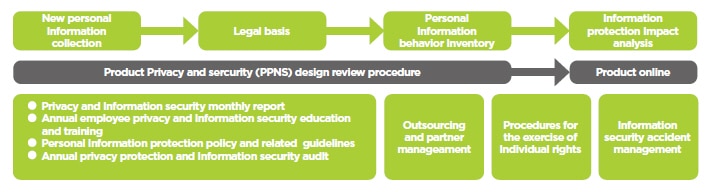
HTC's Privacy Information Management System complies with the Personal Data Protection Act and other international privacy laws and regulations, such as the GDPR of the European Union, the COPPA of the United States, and the CCPA. It also adheres to the relevant specifications of ISO 27701 Privacy Information Management System, ensuring that all business operations are conducted in a legal and ethical manner.
In order to reduce the risk of operation management and ensure the continuous operation of businesses, HTC has moved the core basic systems to the cloud and introduced various cloud services to create a cloud working environment that advances with time. By utilizing the flexibility and high availability of the cloud, deploy and disaster recovery can be performed quickly when failure occurs, effectively improving work efficiency.
Product Information Security
Software Security Control Measures of HTC Products
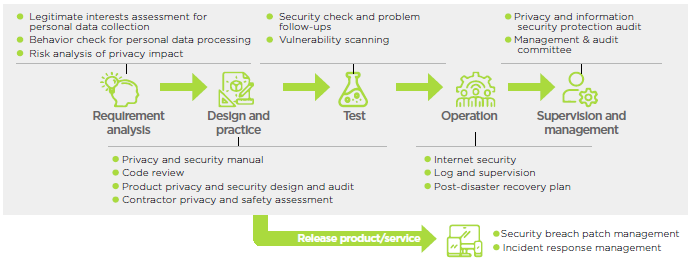
HTC has taken a series of measures to enhance the secure software development framework and management mechanisms of its software products. The company adopts the BSIMM (Building Security in Maturity Model) and related security measures to strengthen control over the secure development of its software products. R&D teams are required to adhere to data security and privacy engineering requirements from the stage of product design. Prior to the release of software products, independent reviews, personal data privacy impact analysis, and security risk assessments are conducted as security controls. Privacy and security auditing workflows (including information security testing, static code scanning tools, vulnerability scanning, and other automated tools) are also introduced. After the products and services are launched, the relevant R&D teams use defect tracking management systems to track the remediation process for software security vulnerabilities. Through continuous integration, the company ensures that the products and services it provides meet the requirements of privacy protection and information security.
In terms of hardware, HTC adopts fingerprint identification systems to reduce the risk of unauthorized individuals accessing products and sensitive personal information, thereby enhancing user information protection. Furthermore, HTC continuously promotes education and training on product development, privacy, and information security. The training content not only makes reference to laws and regulations of various countries but also incorporates industry best practices and HTC's internal contributions and experiences. This strengthens the security awareness, professional capabilities, and product development processes of the R&D teams. By enhancing the employees' knowledge of information security through training, the company reduces security risks as well.
HTC requires that all data collection, utilization, processing, and preservation for its products and services undergo privacy and security review. This ensures compliance not only with international information security standards in the industry but also with applicable laws, regulations, and contractual requirements.
Structure of Product Information Security
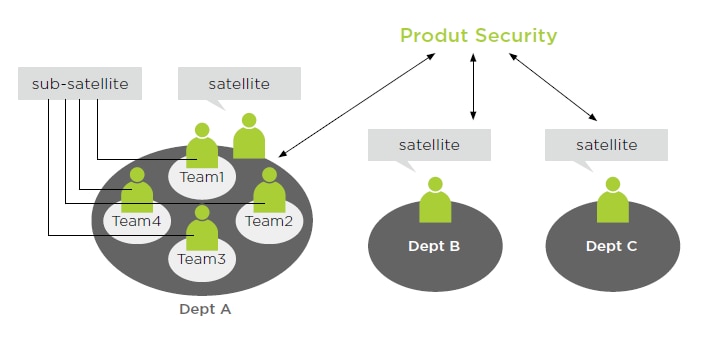
In terms of the product security in the structural planning, we have set up security satellites in major development teams to implement privacy and information security policies more effectively. Besides promoting relevant policies, the security satellites are highly familiar with the products of their own teams and are requested to participate in the PPNS design review procedure mentioned above. Consequently, we enhance the positive meanings of the effect of the review procedure.
In the design and development of software, HTC publishes a privacy protection and safe software development manual to assist the development team for R&D and to execute code reviewing in accordance with the manual. This helps to avoid the involvement of unstable or malicious codes, as well as to ensure that the developed products comply with the expectations of consumers and clients regarding the privacy and information security of HTC’s products.
Our management of privacy and information security goes beyond the launch of products or the sale of devices. HTC requires suppliers to use encryption technology for the transportation and storage of sensitive data and personal information from the procurement of source components. During the use of products, we continuously implement information security controls and track software security vulnerability fixes, before providing them to the R&D teams in charge. In our aftersales service system, we have established information security management procedures that involve authorized personnel handling related information, for which we regularly back up data to ensure its integrity and accuracy.
Attaching great importance to information security incident reported by external researchers, HTC provides dedicated contact channels and a specialized project team to be in charge of receiving, interpreting, and assessing such incidents with prompt responses. We also proactively subscribe to receive news on information security and updates from government agencies, renowned cybersecurity companies, partners, and suppliers in the United States, Taiwan, and other sources. Furthermore, HTC provides internal personnel with appropriate channels to report any observed or suspicious cybersecurity incidents to the specialized project team promptly, aiming to prevent or minimize potential information security incidents.
